IDEA's full name, IntelliJ IDEA, is an integrated environment for Java language development. IntelliJ is recognized as one of the best Java development tools in the industry, especially in intelligent code assistants, code auto-prompt, refactoring, J2EE support, Ant, JUnit, CVS integration. The functions of code review, innovative GUI design, etc. can be said to be extraordinary. IDEA is a product of JetBrains, a company headquartered in Prague, the capital of the Czech Republic. The developers are dominated by rigorous Eastern European programmers.
Introduction to IDEA encryption algorithm1, IDEA encryption algorithm overview
The IDEA encryption algorithm is a block cipher algorithm with a packet length of 64 bits and a key length of 128 bits, which is implemented by 8 iterations. Each iteration consists of three functions: mod (216) addition, mod (216+1) multiplication, and a bitwise XOR algorithm. The whole algorithm includes three parts: subkey generation, data encryption process and data decryption process. The encryption algorithm specifies that both the plaintext and the ciphertext block are 64 bits, the key length is 128 bits, and the encryption and decryption are the same, except that the keys are different.
(1) Encryption process of IDEA encryption algorithm
IDEA performs a total of 8 iterations, requiring 6 subkeys per round, and 4 additional subkey output transforms, so a total of 52 subkeys are required, all of which are extended from 128-bit keys. from.
The input plaintext is 8 characters (ie, 64 bits), and the 64-bit data block is divided into four sub-blocks of X1, X2, X3, and X4, each of which is 16 bits. These 4 sub-blocks will be used as input to the first iteration of the total, with a total of 8 iterations. In each round, the four sub-blocks are XORed, added, and multiplied, and are XORed, added, and multiplied with six 16-bit sub-keys. Finally, 4 sub-blocks and 4 sub-keys are operated in the output transform. The encryption process is shown in Figure 1.
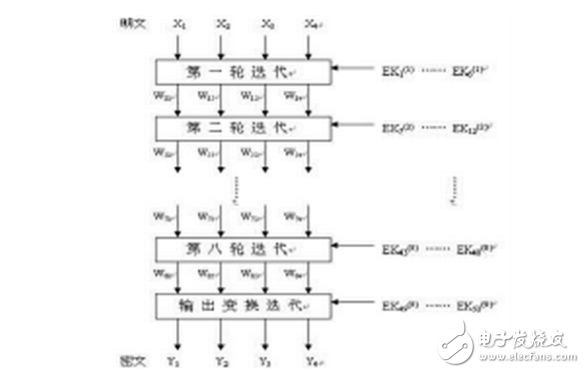
1. Implementation of encryption key expansion algorithm
In the IDEA encryption algorithm, the 128-bit key is actually expanded to 832 bits. Each byte is padded with 16 bits. Specifically how to expand? In the previous expansion idea, it is known that the key string is divided into 8 sub-blocks, and the loop is shifted left by 7 times, wherein the 7th loop is the first 4, so 832 bits (16*8*6+16*4) are finally formed. The extended key array is m_nKeyEncryptBox[52], and some of the code is as follows:
Byte[]asciiBytes=Encoding.Convert(unicode,ascii,unicode.GetBytes(this.m_sEncrypTIonKey));
/ / Encode a set of characters into a sequence of bytes
Char[]asciiChars=newchar[ascii.GetCharCount(asciiBytes,0,asciiBytes.Length)];
/ / Byte to character conversion to string conversion
ascii.GetChars(asciiBytes,0, asciiBytes.Length, asciiChars, 0);
/ / Expanded by the key m_sEncrypTIonKey into an encryption key extension array m_nKeyEncryptBox
For(j=0;j"8;j++)//encryption subkey [j] loop left shift 8+[j+1] bit
Encryption AlgorithmIt was initiated in 1990 by a young Chinese scholar from Switzerland and a famous cryptographer J. Massey. It was officially announced in 1990 and will be enhanced in the future. This algorithm is developed on the basis of the DES algorithm. Similar to Triple DES, IDEA is also a symmetric key algorithm. The development of IDEA is also outdated because of the shortcomings of DES having a key that is too short. IDEA's key is 128 bits, and such a long key should be secure for years to come.

Idea
Similar to DES, the IDEA algorithm is also a block encryption algorithm that designs a series of encryption rounds, each using a subkey generated from a complete encryption key. The difference with DES is that it is as fast as software implementation and hardware implementation.
Since IDEA was proposed and developed outside the United States, it avoids many restrictions on encryption technology in the United States. Therefore, books about IDEA algorithms and implementation technologies can be freely published and exchanged, which can greatly promote the development of IDEA. And perfect
Idea
IDEA is also a major contender for the AES algorithm standard, and its security has been proven at the International Password Conference.
In PGP (pretty good privacy), the IDEA algorithm is adopted.
The 64-bit data packet is divided into four 16-bit sub-packets: xl, X2, x3, x4. These 4 sub-groups become the input to the first round of the algorithm, for a total of 8 rounds. In each round, the four sub-packets are dissimilar, summed, multiplied, and separated from the six 16-bit sub-keys, added, and multiplied. The second and the third sub-packets are exchanged between the wheels and the wheels. Finally, 4 sub-packets and 4 sub-keys are operated in the output transform.
In each round, the order of execution is as follows: (The addition in the following expression refers to the addition of two numbers mod 2^256, for example: (a + b) mod p, the result is a + b arithmetic and division With the remainder of p, that is, (a+b) = kp + r, then (a+b) mod p = r, for example, add "(2)X2 and the second subkey in the following list) "This is the remainder after dividing the sum of X2 and the second subkey by 2^16 (or 65536). For the multiplication in the following expression, it means: (a &TImes; b) mod p, the result is a &TImes; b arithmetic multiplication divided by the remainder of p, and for example, "(1) X1 and the first sub-key multiplied in the following list" means multiplied by X1 and the first sub-key The remainder after (2^16+1) (ie 65537) is accumulated. XOR refers to the non-carry addition.)
(1) X1 is multiplied by the first subkey.
(2) X2 and the second subkey are added.
(3) X3 and the third subkey are added.
(4) X4 is multiplied by the fourth subkey.
(5) Differentiate the results of steps (1) and (3). ·
(6) Differentiate the results of steps (2) and (4).
(7) Multiply the result of step (5) by the fifth subkey.
(8) Add the results of steps (6) and (7).
(9) Multiply the result of step (8) by the sixth subkey.
(10) Add the results of steps (7) and (9).
(11) Differentiate the results of steps (1) and (9).
(12) Differentiate the results of steps (3) and (9).
(13) Differentiate the results of steps (2) and (10).
(14) Differentiate the results of steps (4) and (10).
The output of each round is the four sub-packets formed by the results of steps (11), (12), (13), and (14). After the middle two packets are grouped and exchanged (except for the last round), it is the input of the next round.
After 8 rounds of operation, there is a final output transform:
(1) X1 is multiplied by the first subkey.
(2) X2 and the second subkey are added.
(3) X3 and the third subkey are added.
(4) X4 is multiplied by the fourth subkey.
Finally, the four sub-packets are reconnected together to produce a ciphertext.
It is also easy to generate subkeys. This algorithm uses 52 subkeys (6 for each of the 8 rounds, and the other 4 uses the output transform). First, the 128-bit key is divided into eight 16-bit subkeys. These are the first 8 subkeys of the algorithm (six in the first round and the first two in the second round). Then, the key is shifted to the left by 25 bits and then divided into 8 subkeys. The first four are used in the second round and the last four are used in the third round. The key is again shifted to the left by 25 bits to generate another 8 subkeys, thus completing the D algorithm.
The decryption process is basically the same, except that the subkey needs to be reversed and slightly different. The decryption subkey is either the addition inverse of the encryption subkey or the multiplication inverse. (For IDEA, for modulo 256-one multiplication, all-zero sub-packets are represented by 256=-l, so the multiplication inverse of 0 is 0). It takes time to calculate the subkey, but only once for each decryption key.
Regarding many concepts used in IDEA, you need to refer to the knowledge in number theory. If you have any questions, you can refer to the following materials: computer cryptography (Lu Kaicheng published by Tsinghua University Press), computer cryptography and its applications, elementary number theory, number theory guidance (Hua Luo Geng) and so on. The mathematical principles used in IDEA can be answered in the above materials.
Usb Charger Outlet,Usb Outlet,Usb Plug Socket,Usb Wall Outlet
Lishui Trimone Electrical Technology Co., Ltd , https://www.3gracegfci.com